Cyber Talents Cryptography Challenges
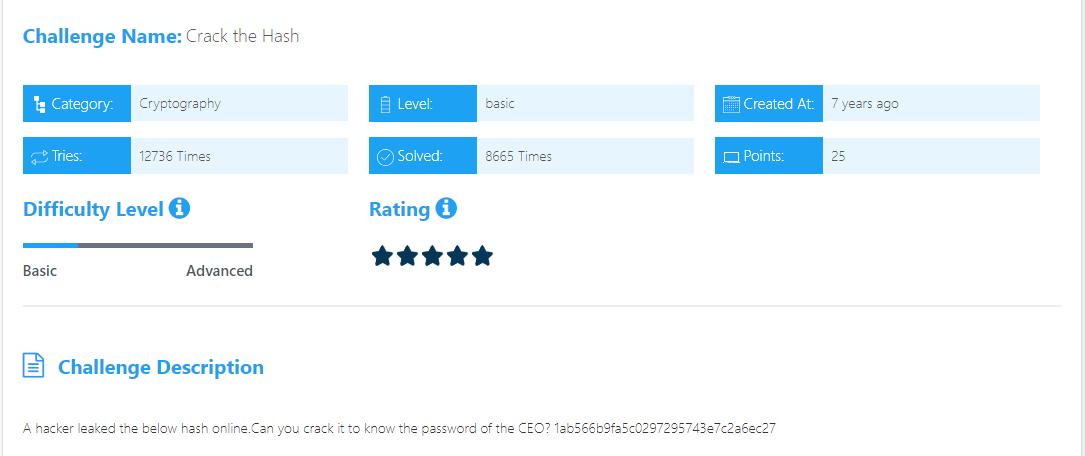
Crack the Hash
First step we need to analyze this hash. We can use Hash Analyzer where we found it is an MD5 hash. We can decrypt it by using MD5 Decryptor.
Solution:
Iamtheflag
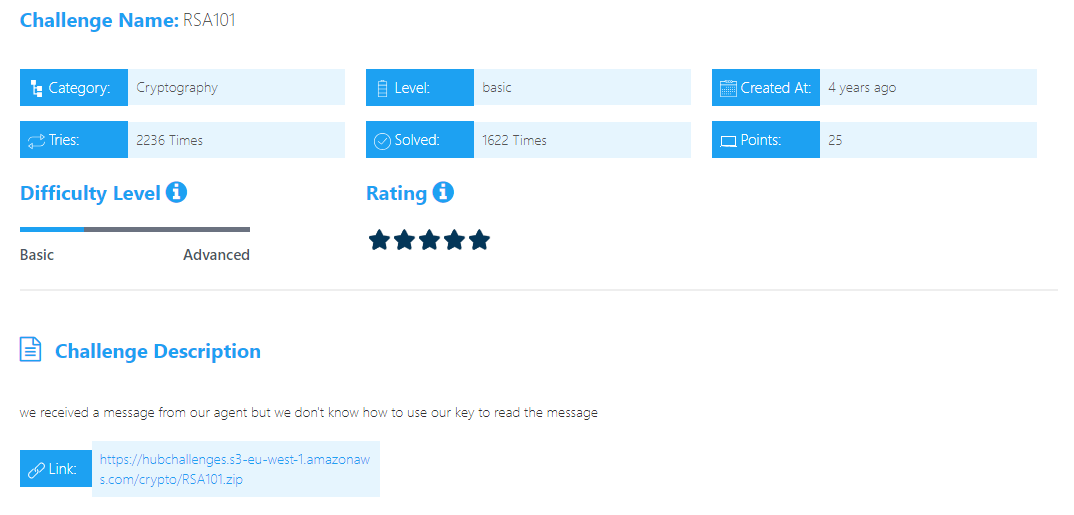
RSA101
After We Extract File we found two file Cipher-Text & Private-Key 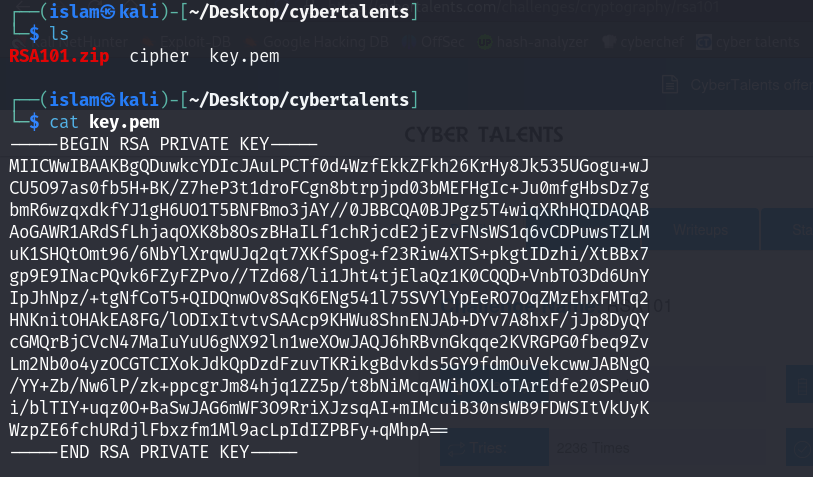 We will use openssl project to decrypt this cipher:
We will use openssl project to decrypt this cipher: 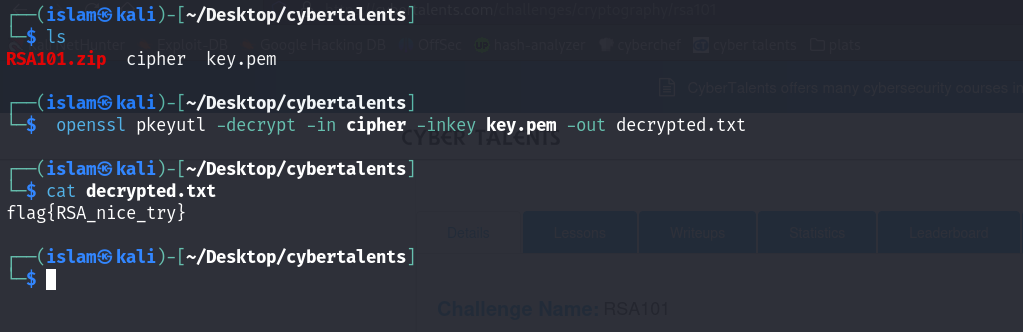
Solution:
flag{RSA_nice_try}
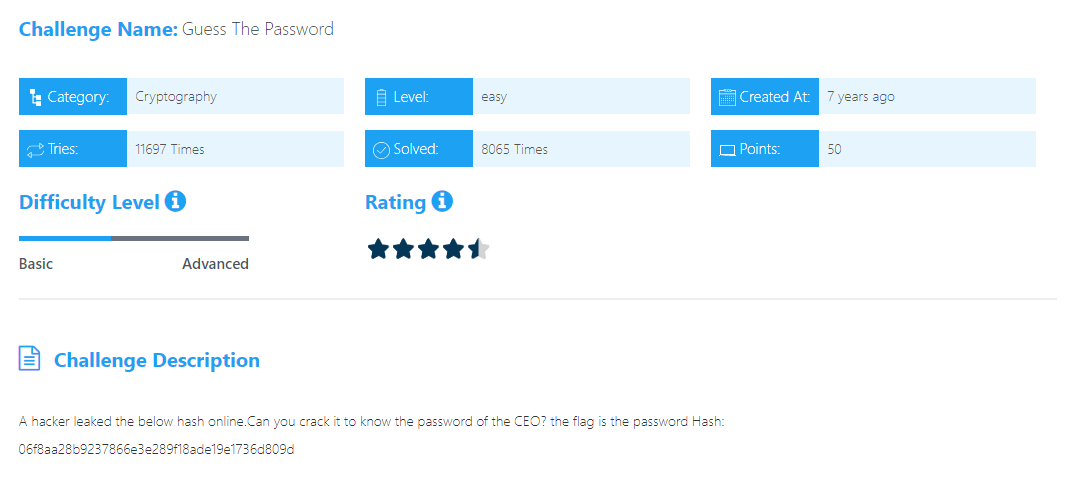
Guess The Password
step1 we need to analyze this hash. We can use Hash Analyzer where we found it is an SHA1 hash. We can decrypt it by using. sha-1 Decryptor
Solution:
jrahyn+
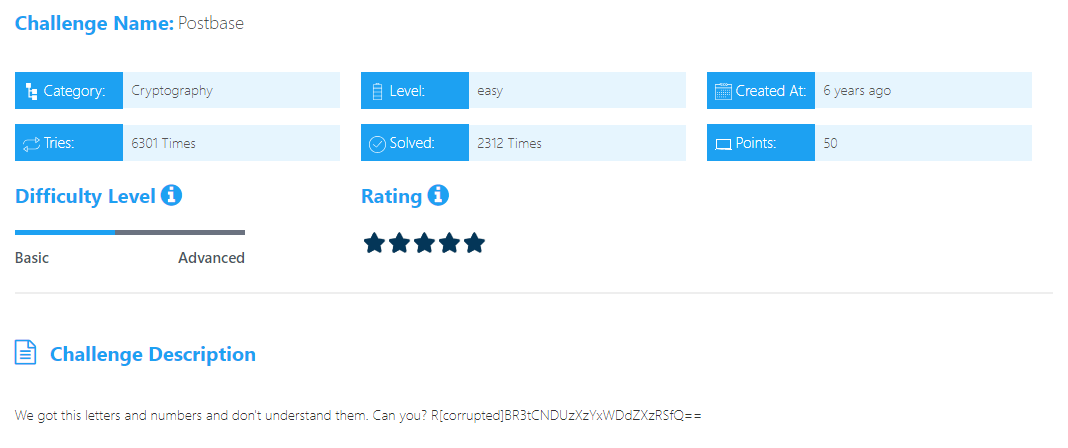
Postbase
First We know the flag format is: flag{xxxxxxxxxxx} R[corrupted]BR3tCNDUzXzYxWDdZXzRSfQ== we want to fix size to 28-bit. We can use Hash Analyzer to know type of hash where we found it is a base64 encoded bruteforce to Reach to format. 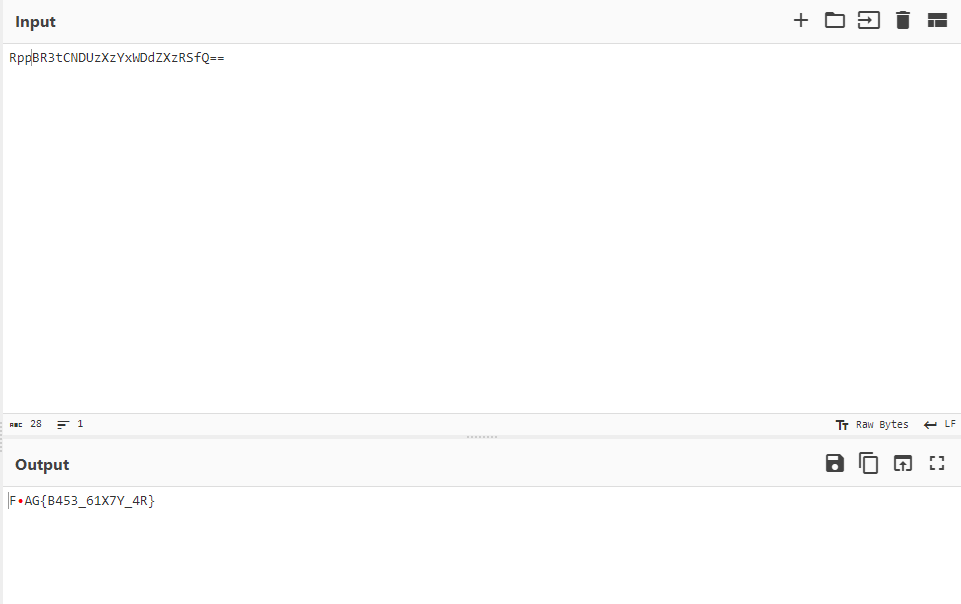
Solution:
flag{B453_61X7Y_4R}
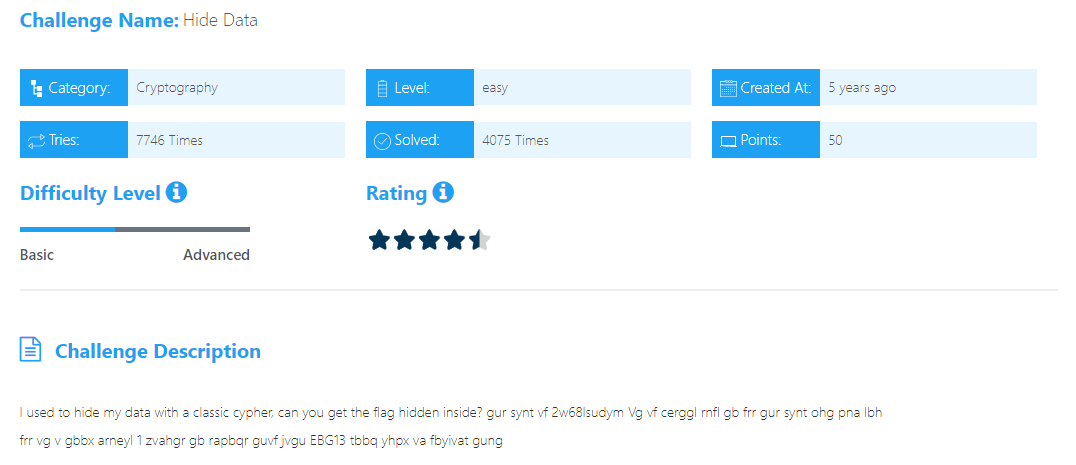
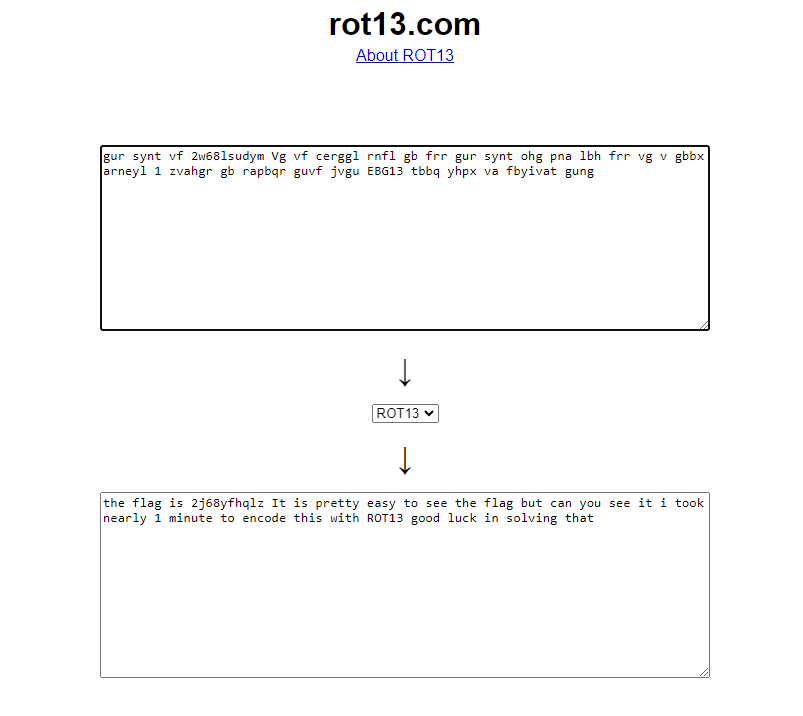
Hide Data
Solution:
2j68yfhqlz
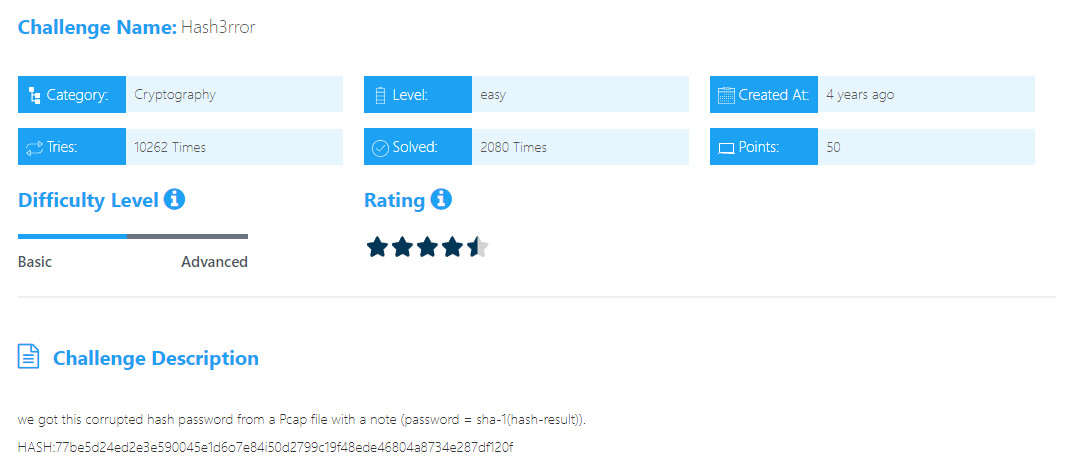
Hash3rror
we have a problem with size fix it to 64-bit by removing two characters not valid o & i after that use Hash Analyzer where we found it is an SHA256. We can decrypt it by using sha-256 Decryptor . 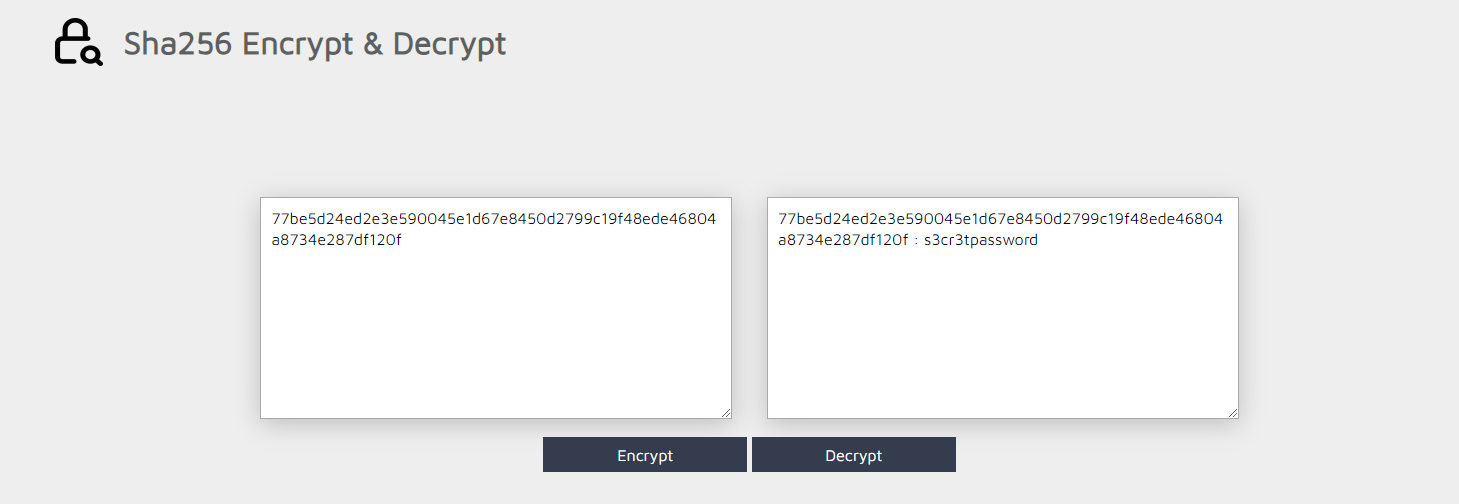 we found this password
we found this password s3cr3tpassword and this note (password = sha-1(hash-result)) let’s encrypt it to sha-1 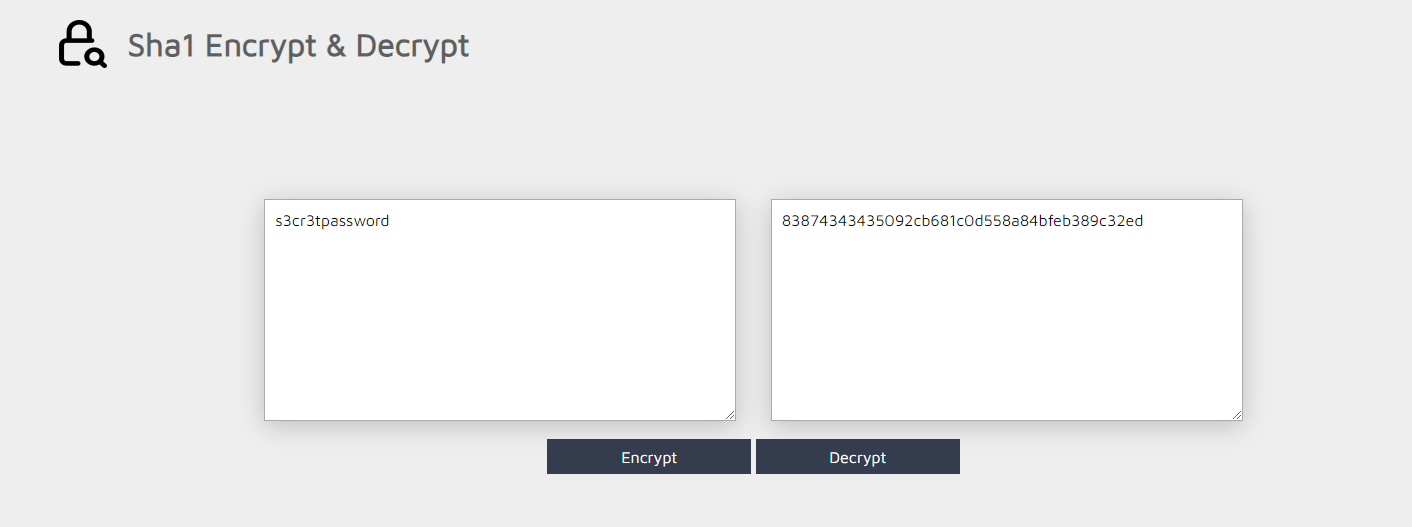
Solution:
83874343435092cb681c0d558a84bfeb389c32ed
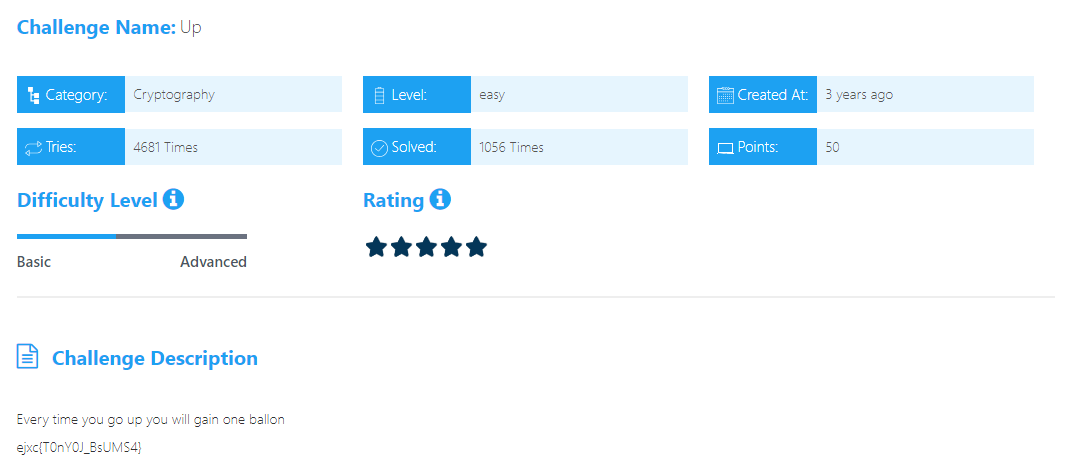
UP
Challenge Description :
Every time you go up you will gain one ballon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
def increment_alphabet_by_index(s):
result = []
ignore_chars = {'{', '_'} # Define ignore characters
shift = 0
for char in s:
if char not in ignore_chars:
shift += 1 # Increment shift for each character except the ignore characters
if char.isalpha():
if char.islower():
new_char = chr((ord(char) - ord('a') + shift) % 26 + ord('a'))
elif char.isupper():
new_char = chr((ord(char) - ord('A') + shift) % 26 + ord('A'))
else:
# For symbols and other characters, do not rotate
new_char = char
result.append(new_char)
return ''.join(result)
# Example usage:
original_string = "ejxc{T0nY0J_BsUMS4}"
new_string = increment_alphabet_by_index(original_string)
print(new_string)
Solution:
flag{Y0uG0T_MeHAH4}
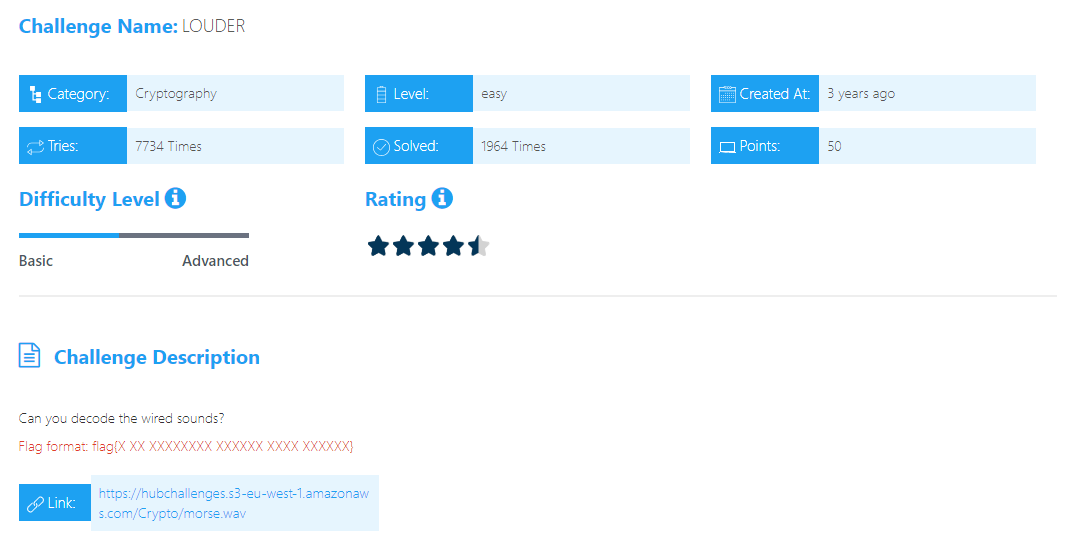
LOUDER
let’s Decode Morse code by: Audio decoder . 
Flag format: flag{X XX XXXXXXXX XXXXXX XXXX XXXXXX}
Solution:
flag{I AM SPEAKING LOUDER THAN BEFORE}
Encoding 1
We need to analyze this message. by Hash Analyzer We found it is an Base64 hash. We can decrypt it by using Base64 Decode.
Solution:
flag{base64_is_n0t_s3cure}
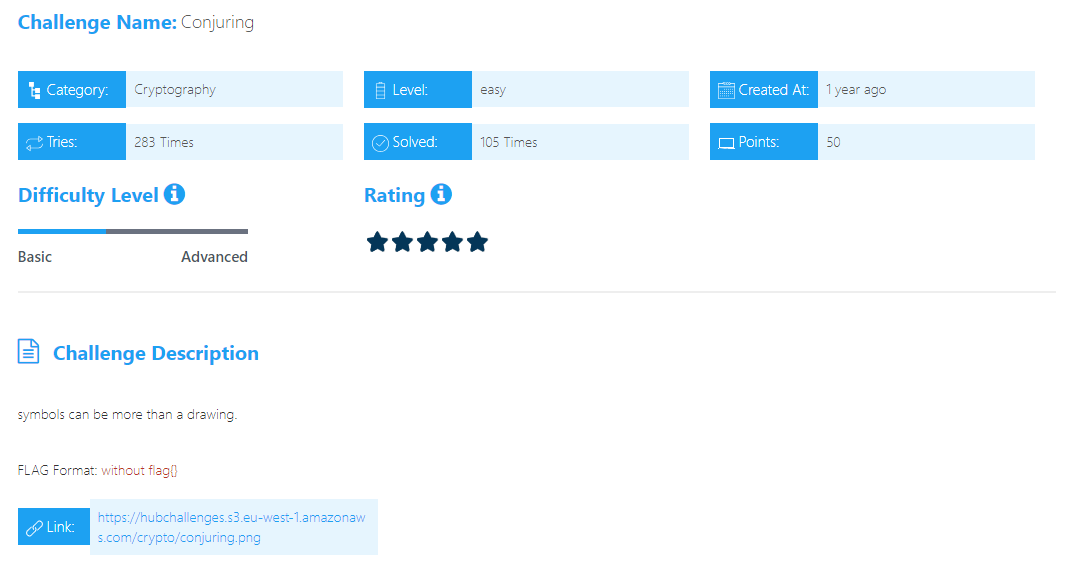
Conjuring
Pigpen Cipher The Pig Pen Cipher, also known as the Freemason Cipher (or masonic alphabet), is an encryption system that was historically used by some members of Freemasonry to protect their communications. 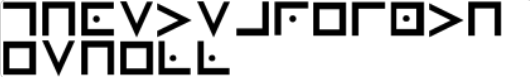 .
.
we can decode it from pigpen-cipher
Solution:
GHOSTSAREINTHESHELL